AWS Landing Zone
Building a Secure and Scalable AWS Landing Zone with AWS Control Tower
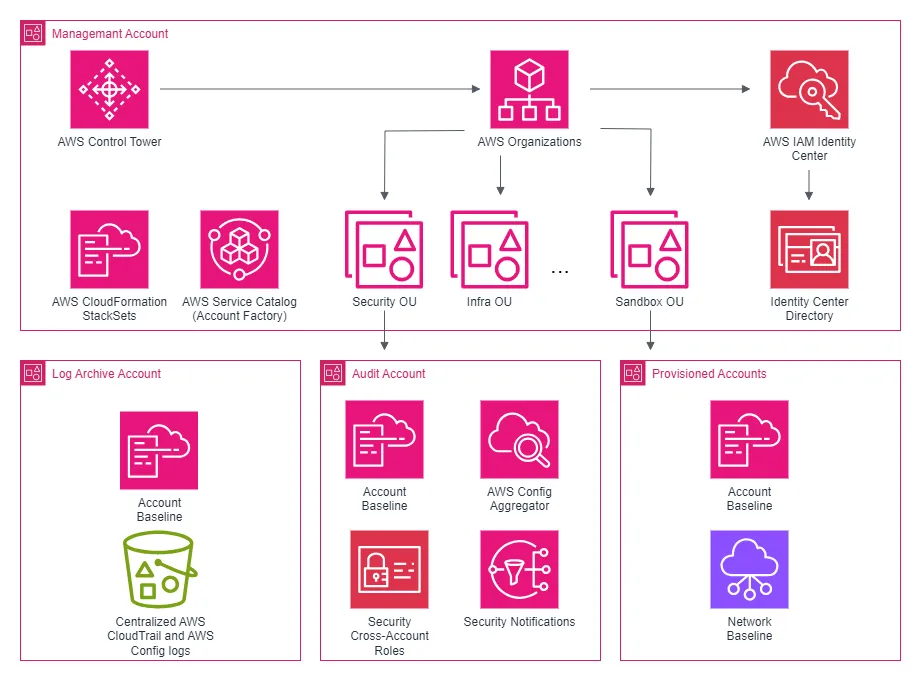 AWS Landing Zone provisioned by AWS Control Tower
AWS Landing Zone provisioned by AWS Control Tower
In today’s cloud-driven world, setting up a secure and scalable environment is crucial for businesses of all sizes. Whether you're an enterprise or a startup, having a structured AWS environment is essential for ensuring security and efficiency. As an AWS expert, I've helped create multiple AWS Landing Zones, and in this article, I’ll share insights on building and optimizing your AWS Landing Zone using AWS Control Tower.
What is an AWS Landing Zone?
An AWS Landing Zone is essentially a multi-account environment within AWS. It allows businesses to launch and manage applications securely while being scalable. Think of it as the foundation where you can confidently deploy your applications, knowing that your infrastructure and security are solid. Setting up a landing zone requires making both technical and business decisions about your account structure, networking, and security.
Challenges with AWS environments before landing zones
Before AWS Landing Zones, managing multiple environments and working with different vendors within a single AWS account posed significant challenges. As businesses expanded, companies needed to manage various applications, services, and vendors within the same cloud infrastructure, leading to new complexities:
- Rapidly growing environments that became difficult to control and organize
- Complications in managing permissions across multiple vendors and environments
- Security risks due to the lack of clear boundaries between environments
- Difficulty in managing service limits, especially with multiple vendors and applications competing for resources
AWS introduced "Organizations" to address these challenges. This solution enables businesses to create isolated AWS accounts for different environments or vendors, all managed centrally under a "management account."
What does AWS Organizations provide?
AWS Organizations offers several essential features that help businesses manage cloud resources across multiple environments and vendors. It allows you to consolidate your cloud infrastructure while maintaining control and security:
- Consolidated billing for all environments and vendors, with potential volume discounts
- Centralized access control through Single Sign-On (SSO) for easier user and vendor management
- Organizational policies to apply consistent security rules across different environments
- A centralized platform for setting up security services and monitoring issues across all accounts and vendors
AWS Organizations forms the foundation for building an AWS Landing Zone, making it easier to manage and scale cloud resources across diverse needs.
Who needs an AWS Landing Zone?
If your business deals with multiple environments or vendors and requires strict security, clear resource management, and efficient isolation, an AWS Landing Zone is essential. It offers:
- Separate security controls for each environment or vendor, ensuring custom policies are applied where needed
- Isolation between AWS accounts to manage multiple vendors and environments without overlap
- Enhanced data protection, allowing sensitive information to remain secured and accessible only to authorized parties
- Improved management of teams, vendors, and their respective responsibilities
- Clear cost management by separating billing for different environments or vendors
- Resource limits to prevent one vendor or environment from affecting others within the AWS infrastructure
What is AWS Control Tower?
AWS Control Tower simplifies the process of setting up and managing your AWS Landing Zone across multiple environments and vendors. It integrates key AWS services like AWS Organizations, AWS Service Catalog, and AWS Identity and Access Management (IAM), creating a secure, multi-account cloud setup quickly and efficiently.
Account structure in AWS Landing Zone
To manage a multi-environment, multi-vendor AWS Landing Zone efficiently, it’s important to follow AWS best practices for organizing accounts and Organizational Units (OUs). Below are the key accounts and optional OUs to consider for your setup:
Shared Accounts
These dedicated accounts serve specific roles to ensure efficient operations, security, and auditing across your AWS environment:
- Management account: The root account of your AWS Organization. This account oversees billing, centralized security controls, and Single Sign-On (SSO). It enforces Guardrails and ensures consistent policies across all environments.
- Log Archive account: Dedicated to logging services like AWS CloudTrail and AWS Config. This account stores logs for all other accounts, providing long-term log retention and secure storage for audit purposes.
- Audit account: Centralized for security services like AWS Security Hub and AWS GuardDuty. This account enforces and monitors security and compliance across all other accounts to ensure the organization's security posture remains intact.
- Shared Services account (Optional): A dedicated account that hosts shared tools such as identity management (IAM), email, DNS, or central DevOps tools like CI/CD pipelines. This account allows for the management of services used across multiple environments or vendors.
- Backup account (Optional): Used for managing backups across the AWS environment. It is isolated to ensure that backup data is secured and managed independently from production environments.
Organizational units (OUs)
AWS best practices recommend organizing accounts into OUs for better governance and management. Here’s an outline of standard and optional OUs for a multi-environment, multi-vendor setup:
- Infrastructure OU: This OU contains accounts for core shared infrastructure services like networking, DNS, and DevOps tools. It ensures that essential services are available across all environments.
- Workloads OUs: These OUs organize accounts based on environments (e.g., Production, Staging, Development) or based on specific applications or workloads. This structure ensures isolation and limits the scope of any failures or security risks.
- Sandbox OU: A separate OU where developers, testers, or vendors can experiment and test without impacting production. These accounts are often budget-restricted and isolated from core networks for security.
- Suspended OU: An OU for accounts that are locked down due to security issues or are in the process of being closed. Accounts in this OU are restricted through Service Control Policies (SCPs), which block all actions.
- Security OU: This OU can be used to contain security-focused accounts, such as those used for audit, incident response, or penetration testing. It helps keep security operations isolated from regular workloads.
- Business Unit OU (Optional): For larger organizations with distinct departments or business units, you can create OUs based on organizational functions (e.g., Finance, Marketing, Sales) to separate and manage resources more effectively.
- Vendor OU (Optional): If you work with multiple vendors, you can create a dedicated OU for each vendor, ensuring that vendor accounts are isolated from internal environments and follow specific access or billing controls.
- Development Tools OU (Optional): An OU specifically for accounts that host DevOps tools, build systems, or code repositories. This OU ensures that development tools are isolated from production systems.
By structuring your AWS accounts and OUs according to best practices, you can ensure better governance, security, and efficiency across multi-environment, multi-vendor scenarios. Whether you're managing core infrastructure, separating workloads, or setting up accounts for vendors, following this approach provides clarity and control over your AWS environment.
Control Tower Guardrails
AWS Control Tower offers "Guardrails," which are security rules that help you govern and manage multiple environments and vendors. These Guardrails can either detect non-compliant actions or prevent them entirely, helping maintain compliance across all cloud operations.
With over 500 Guardrails available, AWS Control Tower provides a flexible and powerful toolset for monitoring and enforcing security policies across various regions and environments.
Management account: the control center
The Management account is your central hub for managing all other AWS accounts in your Landing Zone. It controls billing, user access, and security policies. This account acts as the brain of your cloud operations, and here are some ways it helps you maintain order:
- Centralized billing: You get a clear view of costs from all your AWS accounts, which is crucial for managing your budget and identifying potential cost savings.
- Security Guardrails: AWS Control Tower automatically sets up preventive measures called Guardrails, which help you enforce security policies across all accounts. This means you don’t have to worry about teams bypassing important security protocols.
- SSO (Single Sign-On): AWS Identity Center (previously AWS SSO) is preconfigured to manage access securely. You can integrate with your existing identity provider like Microsoft AD, Okta, or Google, making it easier to manage user roles and permissions across the organization.
Best practice: Keep this account strictly for management purposes. Avoid deploying workloads in the Management Account to ensure a clear separation of concerns, keeping governance and operations distinct.
Log Archive account: your compliance backbone
The Log Archive account is designed to store logs from all your AWS resources. Think of it as your compliance and security backup, ensuring that every action across your AWS environment is recorded and ready for review when needed.
Logs from services like AWS CloudTrail (which tracks API activity) and AWS Config (which monitors resource configurations) are automatically stored in this account. This centralized logging ensures that all your compliance needs are met, and it simplifies audits when your security or legal teams need to investigate any issues.
- Centralized logging: Storing all logs in one place makes it easier to manage and analyze activity across your entire cloud environment.
- Enhanced security: Restrict access to this account to compliance or security teams to ensure that only authorized individuals can view sensitive logs.
Best practice: Integrate a central monitoring tool to analyze these logs. This can help identify suspicious behavior and ensure rapid incident response.
Audit account: the watchdog for security
The Audit account gives your security and compliance teams read and write access across all your AWS accounts. It’s built for monitoring and auditing, ensuring that all your accounts follow the necessary security guidelines and compliance standards.
The Audit Account allows programmatic access to your entire AWS environment without manual intervention, making it perfect for automation. For instance, you can set up AWS Config rules or security checks that automatically monitor your resources and generate reports on potential issues.
- Cross-account auditing: This account provides access to all other accounts, allowing security teams to run automated checks and audits without manually logging into each account.
- Security Hub Integration: AWS Control Tower enables Security Hub on the Management Account, while the Audit Account acts as the administrator for services like AWS GuardDuty, Macie, and Inspector, ensuring a comprehensive security setup.
Best practice: Automate as much as possible. Use tools like AWS Security Hub and GuardDuty to constantly monitor your AWS environment for threats, and integrate alerting system for notifications.
Centralized backups: protecting your data
One of the essential components of an Infrastructure OU is centralized backup management. A robust backup strategy protects your business in case of data loss, ransomware attacks, or other disasters. AWS provides automated solutions through the AWS Backup service, allowing you to configure backup policies across multiple accounts.
- Disaster recovery: By copying backups to a different AWS region or even another AWS account, you reduce the risk of losing access to critical data during a regional failure or unauthorized access.
- Backup policies: You can create backup schedules, retention policies, and cross-account copy actions that are enforced centrally, ensuring that critical resources across all your accounts are backed up automatically.
Best practice: Regularly review and update your backup policies to ensure they meet your organization’s recovery point objectives (RPOs) and recovery time objectives (RTOs). Use the Infrastructure OU to centralize and automate these backups for consistency and security.
DevOps account: centralizing development tools
The DevOps account is crucial for managing CI/CD tools like Jenkins, GitLab, and AWS CodePipeline. Centralizing these tools in a dedicated account makes it easier to manage deployments and enforce security best practices across multiple environments and teams.
- CI/CD Tools: By deploying your CI/CD pipelines centrally, you can control deployments to different environments from one place, ensuring consistency in the development lifecycle.
- Artifact storage: Tools like Amazon ECR or Artifactory can be used to store build artifacts, ensuring they are secure and accessible to all your teams.
Best practice: Limit access to the DevOps account to your development teams and ensure that security practices such as role-based access control (RBAC) are enforced through AWS Identity Center or other identity providers.
Shared services: centralizing monitoring and logging
The Shared Services account serves as a central repository for all monitoring and logging tools. It helps you track performance, detect issues, and respond to incidents across your AWS environment, making it a key part of any Infrastructure OU.
- Centralized monitoring: Use tools like Amazon OpenSearch or Prometheus to centralize application logs and metrics. This allows your support teams to access logs from all environments in one place, simplifying troubleshooting and incident management.
- Cross-environment visibility: Centralized logging enables visibility across all environments (production, staging, etc.), helping you detect issues faster and streamline the resolution process.
Best practice: Implement monitoring and alerting for critical services using AWS CloudWatch and integrate with third-party tools such as Slack or PagerDuty for real-time notifications.
Networking account: centralized and secure networking
Networking is one of the most critical components in your AWS environment. With a dedicated Networking account, you can centralize all networking operations, including VPCs, DNS, IP management, and traffic routing, ensuring secure and scalable network infrastructure.
- IP Address Management (IPAM): Use IPAM to manage, track, and monitor your IP addresses across multiple AWS accounts and regions. This ensures that your IP address space is well-organized and easily scalable.
- Central Transit Gateway: A Transit Gateway connects your VPCs and on-premises environments, acting as a centralized router that simplifies network management. The network team can use AWS tools like EventBridge and Lambda to automate VPC attachments and updates.
- Firewall Security: Deploy a centralized firewall to inspect and filter traffic across all VPCs. This ensures that all network traffic is securely monitored, preventing unauthorized access and potential security breaches.
Best practice: Always segment your network using subnets, security groups, and network ACLs to create isolated environments. Automate the network configuration using AWS solutions like Network Orchestration for AWS Transit Gateway to simplify VPC management.
Optional Organizational Units (OUs) for flexibility
To further enhance your AWS Landing Zone, you can implement additional optional OUs based on your organization’s unique needs:
- Security OU: A dedicated OU for managing security-focused accounts that handle audits, penetration testing, and security automation. This ensures that all security operations are isolated from regular workloads.
- Business Unit OU: For organizations with distinct departments or business units, creating OUs based on function (e.g., Marketing, Finance) helps separate resources and control access more effectively.
- Vendor OU: If your company works with multiple vendors, you can create an OU to manage vendor-related accounts, ensuring they are isolated and properly managed with limited access.
- Development Tools OU: Centralizes all development-related tools and resources in a dedicated OU, ensuring that DevOps tools, code repositories, and build systems are isolated from production environments.
Control Tower Guardrails
In any multi-account AWS environment, maintaining security and compliance is a top priority. AWS Control Tower makes this easier by offering built-in governance mechanisms called Guardrails. These Guardrails help you ensure that your organization’s cloud resources are managed according to best practices.
Here is a breakdown of the three main types of Guardrails that AWS Control Tower provides: Detective, Preventive, and Proactive controls. We’ll explore how each one works, along with practical examples of how you can use them to keep your AWS environment secure.
Detective controls: monitoring for compliance
Detective controls focus on identifying and alerting you to any non-compliant resources or actions within your AWS environment. These controls don’t stop actions from occurring but notify you when something isn’t aligned with your policies.
Detective controls are implemented using AWS Config rules, which continuously check the configuration of your resources. For example, a detective control can alert you if an Amazon EC2 instance is running with an unencrypted EBS volume.
- Example: Let’s say you have a detective control that checks whether encryption is enabled for EBS volumes. If a user creates an EC2 instance with an unencrypted volume, AWS Config will flag this as non-compliant and alert you through the Control Tower dashboard.
- Practical use: These controls are excellent for auditing and ensuring that your teams follow the organization’s security policies. They provide visibility into resources that might pose a security risk.
Best practice: Regularly review your detective controls and make sure they cover critical resources like storage, networking, and databases. Use AWS Config rules to automate compliance checks across all accounts.
Preventive controls: stopping non-compliant actions
Preventive controls go a step further by actively blocking actions that would lead to non-compliance. These controls are enforced through Service Control Policies (SCPs), which are applied to entire Organizational Units (OUs).
When a preventive control is enabled, AWS prevents users from performing certain actions that could violate your policies. For example, a preventive control can ensure that public access to sensitive resources like EBS snapshots is automatically blocked.
- Example: Suppose you enable a preventive control to disallow making unencrypted EBS snapshots public. This control ensures that if a user attempts to share an unencrypted snapshot publicly, AWS will block the request and enforce compliance.
- Practical use: These controls are perfect for stopping potential security issues before they happen. They ensure that critical actions, such as exposing sensitive data, are never allowed.
Best practice: Use preventive controls for actions that could lead to significant security risks, such as sharing unencrypted data or modifying network configurations. Apply them broadly across your Organizational Units to prevent accidental breaches.
Proactive controls: ensuring compliance before deployment
Proactive controls are designed to prevent non-compliant resources from being created or updated in the first place. These controls are enforced through CloudFormation hooks, which check for compliance during resource creation or update operations.
Proactive controls ensure that infrastructure-as-code deployments adhere to your organization’s security and compliance policies. For instance, you can use a proactive control to ensure that all Amazon S3 buckets enforce HTTPS-only communication.
- Example: A proactive control can check whether an S3 bucket allows data transmission over HTTP. If a user attempts to deploy a non-compliant bucket, the CloudFormation stack will fail, preventing the creation of the insecure resource.
- Practical use: These controls are invaluable for organizations that use CloudFormation or other Infrastructure-as-Code (IaC) tools. They ensure compliance is enforced before resources are even created, reducing the risk of misconfigurations.
Best practice: Use proactive controls for critical resources like S3 buckets and databases, where security must be enforced from the moment of deployment. Proactively checking resources ensures they meet your standards before they are launched.
Optional organizational units for enhanced security
You can further improve security and compliance across your AWS Landing Zone by leveraging optional OUs alongside these Guardrails:
- Security OU: A dedicated OU for security-related tasks such as audits, incident response, and compliance monitoring. This can include accounts that handle tools like AWS Security Hub, GuardDuty, and Inspector.
- Development OU: By separating development environments from production, you can use specific Guardrails to enforce stricter policies in production while allowing flexibility in development and testing accounts.
Best practice: Customize your Organizational Units to match the structure of your organization. Apply stricter controls to production OUs while maintaining flexibility in sandbox or development OUs.
Further customization of your AWS Landing Zone
Every organization has unique requirements when it comes to cloud infrastructure. Customizing your Landing Zone allows you to meet these specific needs while ensuring that your infrastructure remains scalable, secure, and aligned with AWS best practices.
- Streamlined Deployments: Using custom templates and automation, you can deploy resources consistently across multiple AWS accounts without manual intervention.
- Enforce Security: Custom SCPs allow you to enforce security policies that prevent risky actions, such as disabling critical logging services or allowing public access to sensitive data.
- Maintain Control: CloudFormation and CodePipeline ensure that all deployments are reviewed, tested, and approved before going live, giving you confidence in the integrity of your infrastructure.
Best practice: Regularly review your customizations to ensure they remain aligned with your evolving business needs. Using automation and approval stages within CodePipeline adds an extra layer of control to ensure that changes are reviewed before impacting production.
How to deploy customizations
Customizations for AWS Control Tower (CfCT) allow you to manage your Landing Zone resources efficiently using a combination of CloudFormation templates, SCPs, and AWS CodePipeline. Here's a simplified process for deploying these customizations:
Step 1: Set up CloudFormation templates
Start by defining the infrastructure and policies you want to deploy in your Landing Zone. For example, you can create templates for S3 buckets, VPCs, or specific security configurations like preventing the deletion of flow logs.
- Example: Create a CloudFormation template to deploy a centralized S3 bucket for VPC FlowLogs in your Log Archive account. This ensures that all VPC traffic is logged and stored securely, helping you meet compliance and audit requirements.
Step 2: Use AWS CodePipeline for automation
CodePipeline is a crucial component of the customization process. It automates the deployment of your CloudFormation templates and SCPs across multiple AWS accounts, ensuring consistent configuration. You can include manual approval stages to ensure that all changes are reviewed before being applied to production environments.
- Pipeline example: After pushing your configuration code to the CodeCommit repository, CodePipeline triggers the build, validates the CloudFormation templates, and awaits approval before proceeding to deploy the resources to the target accounts.
- Manual approval: By enabling manual approval stages, you can ensure that no changes go live without review. This is critical for maintaining control over sensitive production environments.
Best practice: Always include a manual approval stage in your pipeline for production environments. This ensures that no unreviewed changes are made to critical resources.
Step 3: Service Control Policies (SCPs)
SCPs are a key feature of AWS Organizations that help you enforce security and compliance policies across your accounts. With CfCT, you can deploy custom SCPs alongside your infrastructure to restrict actions that may pose security risks.
- Example: Deploy an SCP that prevents users from disabling VPC Flow Logs. This ensures that traffic logging remains active at all times, helping you maintain visibility into network activity for security and compliance purposes.
Best practice: Use SCPs to lock down critical configurations such as logging, network security, and resource access. Apply these policies broadly across your Organizational Units to enforce compliance.
Step 4: Deploying infrastructure
Once your templates and SCPs are ready, CodePipeline deploys the resources in the correct order. For example, you might first deploy an S3 bucket for VPC FlowLogs, followed by a VPC in the production environment that uses the previously created S3 bucket for logging.
- Example: Deploy a VPC in the production account, using a previously created IPAM pool for CIDR allocation and the S3 bucket for logging. This ensures that your network infrastructure is set up correctly, with logging enabled from the start.
Advanced customization tips
Here are a few tips to get the most out of your Control Tower customizations:
- Parameter passing: Use AWS Systems Manager (SSM) Parameter Store to pass outputs between different CloudFormation stacks. For example, the S3 bucket name created in one stack can be passed to another stack to enable logging for a VPC.
- Security first: Always prioritize security in your customizations. Enforce encryption, logging, and access controls through SCPs and CloudFormation templates to prevent misconfigurations.
- Automation: Leverage automation as much as possible, but always include human oversight where necessary, especially in production environments.
Final thoughts
The modularity offered by AWS Control Tower, combined with the ability to customize OUs, SCPs, and automation pipelines, provides the flexibility needed to tailor your cloud setup to your organization's specific needs. By adopting a well-structured approach—whether it's isolating workloads, protecting critical resources, or integrating shared services—you can confidently scale your AWS environment.
If you need assistance with AWS services to meet your business needs, feel free to reach out.